20+ cyber security diagrams
The Microsoft Cybersecurity Reference Architectures MCRA describe Microsofts cybersecurity capabilities. List of 22 data flow diagram cyber security Blog By Admin 1Process Flow vs.

Subareas Of Cybersecurity Download Scientific Diagram
Modernize your security strategy approach to survive the era of remote work and beyond.

. The most Simple and Yet Powerful SIEM Solution to all Log Management and Security Needs. Data Flow Diagrams for Threat Modeling Table of Contents 1 Process Flow vs. The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart shapes icons and.
A Top 20 DBT diagram for a hypothetical water treatment plant is illustrated in Figure 1. Data Flow Diagrams for. You can edit this template and create your own diagram.
Flexible Schedules Coursework Aligns with Leading Industry Certification Exams. Ad Embracing a Zero Trust Security Model. Designed by the Center for Internet Security after the US defense industry experienced a data breach in 2008 the CIS 20 is a series of 20 controls deemed critical to.
The Top 20 ICS cyber security attacks are. Use PDF export for high. Multiple Layers of Protection for Cyber Security.
Ad Real time Security Information Event and Management software. Protect against Insider Risk to prevent employee departure from becoming data departure. A cloud and remote work security strategy.
1 Use Case Diagram Smart Building Use Cases. In this article. Ad Learn Cybersecurity Enterprise Security Information Assurance Cryptography More.
These network infrastructure diagrams are essential to any cybersecurity program. Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple. 1 Use Case Diagram Smart Building Use Cases.
The top 20 use case diagram for cyber security. Ad Learn Cybersecurity Enterprise Security Information Assurance Cryptography More. Creately diagrams can be exported and added to Word PPT powerpoint Excel Visio or any other document.
Figure 3 shows the contest area which is composed of a cage for the cyber-physical security honeypot made from plastic orange construction fence in order to ensure the safety of DEF. The diagrams describe how Microsoft security. 1 ICS Insider A disgruntled control-system.
Join us to discover how to protect you and your business from the 1 cause of cyberattacks. Cybersecurity classic by jeremiah Marcoe. Without this information CISOs and security advisors cannot identify system.
Ad 98 of business leaders report having data security concerns with employee turnover. Ad Comprehensive Antivirus Online Security Identity Theft Protection. Flexible Schedules Coursework Aligns with Leading Industry Certification Exams.
Blog By Admin. Ad Discover security thats engineered to beat social engineering - the 1 cause of breaches.

Cyber Security Dynamics 20 Download High Resolution Scientific Diagram
Cybersecurity Taxonomy For Iiot Download Scientific Diagram

Saudi Cybersecurity Maturity Assessment Framework Scmaf Full Size Download Scientific Diagram

Iec 62443 Cybersecurity Process Steps Download Scientific Diagram

Diagram Of Cyber Security Investment Decisions Inputs And Outputs Download Scientific Diagram
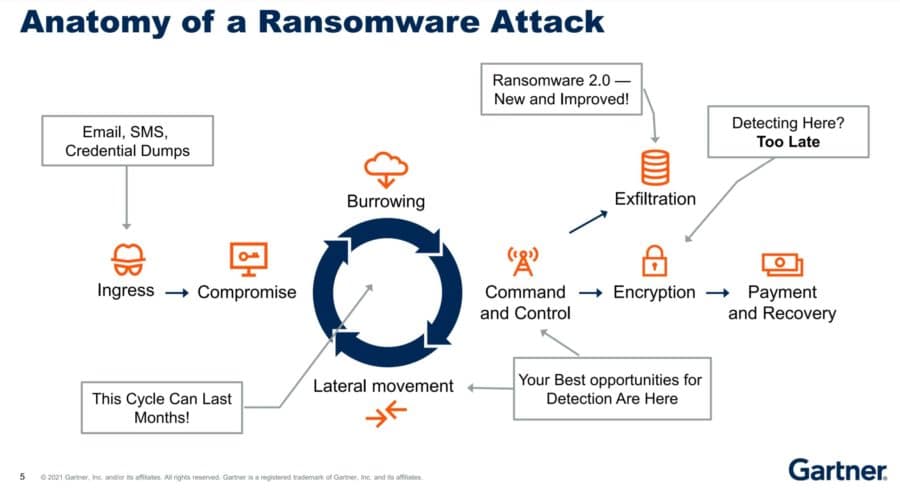
Cybersecurity Mesh And Decentralized Identity Explained
High Level View Of The Cybersecurity Taxonomy Download Scientific Diagram

Timeline And History Of Ics Cybersecurity Attacks Download Scientific Diagram
The Schematic Diagram Of The Hybrid Cyber Attack Download Scientific Diagram

Reference Architecture For Next Generation Cyber Security Frameworks Download Scientific Diagram

Cybersecurity Key Components And Relationships Download Scientific Diagram

Network Diagram Of The Interdisciplinary Nature Of The Field Of Social Download Scientific Diagram

Predictive Model For User Cybersecurity Behavioral Intentions Note Download Scientific Diagram

Illustration Of Cyber Security In Smart Grids Download Scientific Diagram

The Logical Architecture Of The Cybersecurity Situation Awareness Download Scientific Diagram

Illustration Of Cyber Security In Smart Grids Download Scientific Diagram
Timeline And History Of Ics Cybersecurity Attacks Download Scientific Diagram